This article will show how to investigate and suspend illegal CSAM or revenge porn websites. This is the first time I’ve done a non-investigative article. so it will be shorter than normal.
These are my techniques for collecting information and metadata from websites and then submitting abuse reports.
Find domain information using whois collections:
When you see a website that is illegal or contains illegal material such as illegal pornography, the first thing you have to do is investigate the domain
In this case I will use the digital whois tool, and I will use the domain example.com as an example to show how to do this.
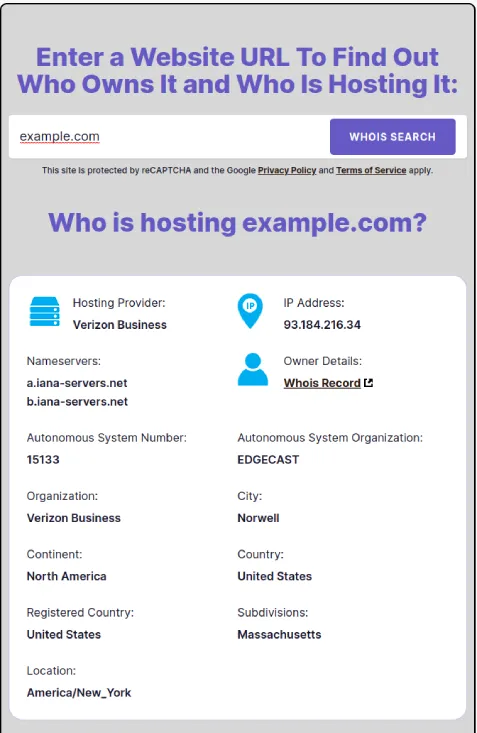
This tool gave us information about the name of the hosting company, IP, nameservers, ASN and whois information. With this information we can investigate more about the domain using OSINT.
This is an example, depending on the company that appears to you, you have to add “*youcompanyname* report abuse” in Google Search. You will find different ways to contact a hosting company for an abuse report easily
- Tool: Digital Whois
information about the infrastructure and servers of a website:
Now that we have the IP information, we are going to analyze the ipv4 that the website is using to store the illegal content.
With the online tool called IPalyzer we can analyze the ipv4 address more deeply, we will collect a lot of information about the network infrastructure of the selected website
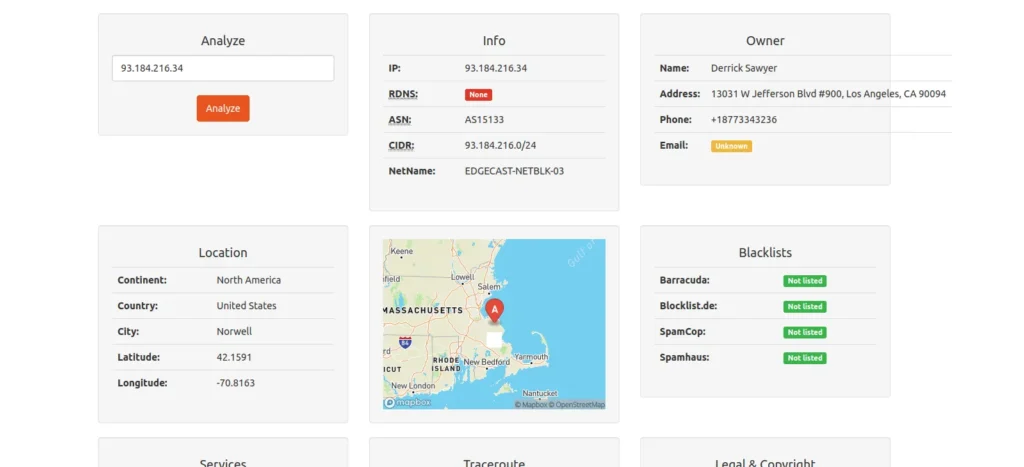
With this tool we were able to collect information such as the ASN, GeoLocation, information from the owner of the infrastructure of the hosting company and search for information from blacklists.
IPv4: 93.184.216.34
ASN: AS15133
CIDR: 93.184.216.0/24
Network Name: EDGECAST-NETBLK-03
Other Information: Location , Geolocation , Blacklist check , Owner info.now with the ipinfo tool we will analyze the ASN (Autonomous System Lookup) that is using the ipv4 of example.com
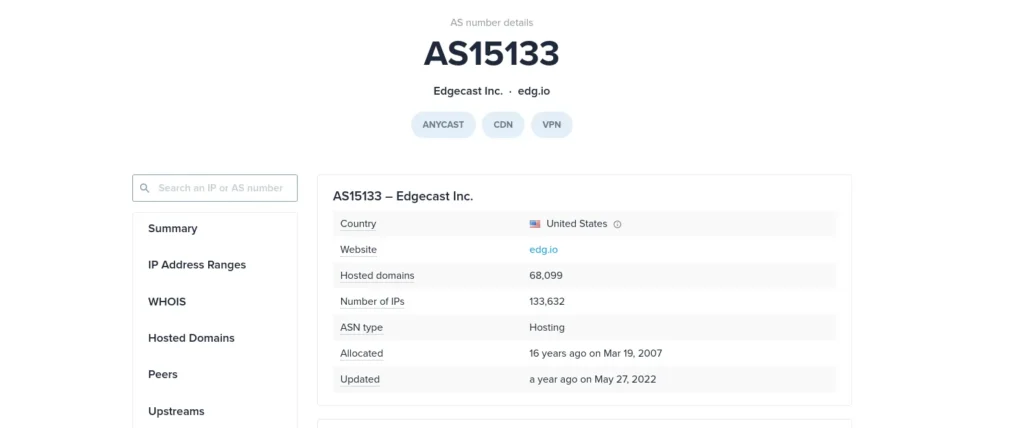
in the photo you can collect the name of the company that uses the infrastructure. In the whois section you can find the official abuse email.
once the abuse email is obtained, you just have to alert them that there is an illegal website using the servers company
Tools:
get the information of the domain company of an domain:
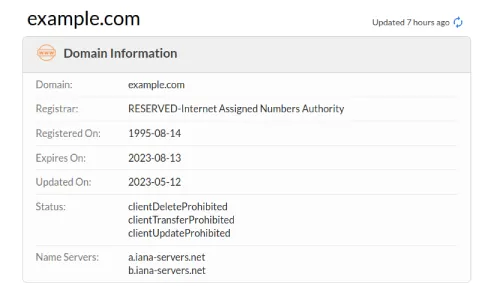
Using the ICANN service called ICANN Lookup we will be able to observe domain information such as the status , creation date and domain registrara company.
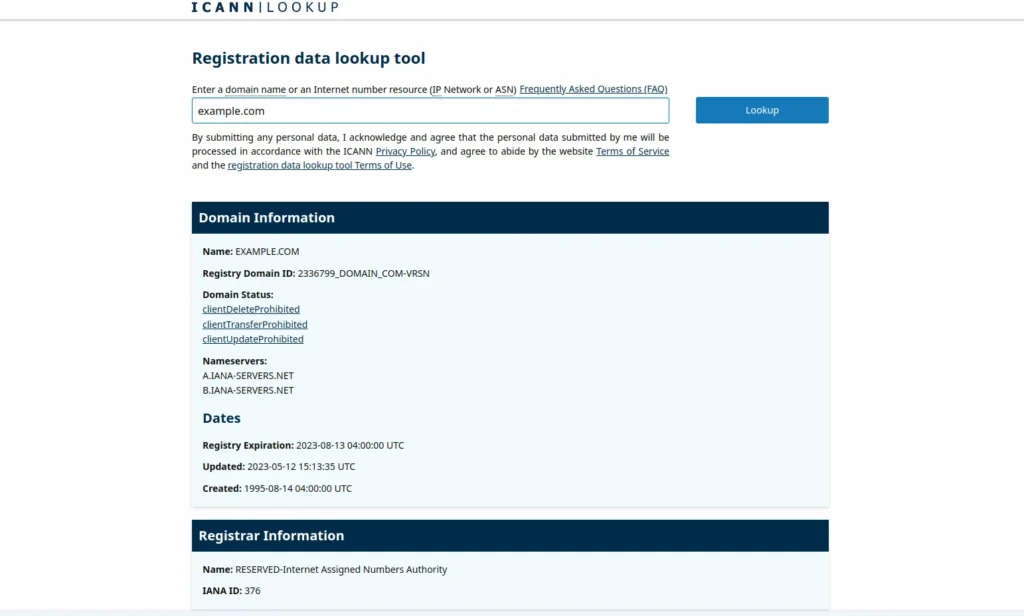
In the registration information, the name and IANA ID appear, which is the ID of the company or domain registrant in the IANA database.
Once we have the registrant information in the register information section, we go to Google Search and look for the name of the domain company + “report abuse” and you will find the email information.
in this case, ICANN is the registrant owner of example.com is ICANN itself, so it is an authoritative and trusted domain.
for example, this domain that I will not name. the registrant is Google LLC and the abuse contact is listed there.
alternative to ICANN lookup services:
ICANN service is good, the problem really is that ICANN doesn’t test certain domains, so an alternative is the online tool called whois.com/whois
in this case, whois.com does not allow access to information from special domains of countries, such as .ru, .uk, .kr, .es, and among others.
Therefore, unlike ICANN Lookup, here we will have more domains available to collect information and the contact to report abuse.
This whois tool, like ICANN Lookup, is fully accessible to everyone and they are 2 good tools for collecting OSINT data related to Internet domains.
collect info about a DNS server and DNS Zone of a domain:
a DNS server or a DNS zone are often part of a website infrastructure, and most often do not use the same hosting or domain company.
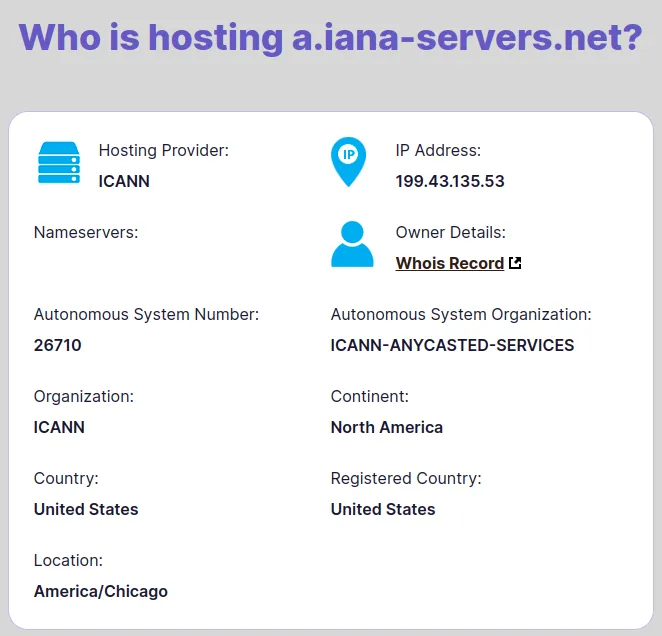
In this case, the DNS server is owned neither by Verizoon Bussines nor by EDGECAST in, the hosting company for example.com DNS is ICANN.
- Tool: Digital Whois
and the domain is owned by the ip address organization called IANA. In the event that example.com was a suspicious or illegal domain, 2 abuse reports could be sent to these 2 organizations that own the infrastructure.
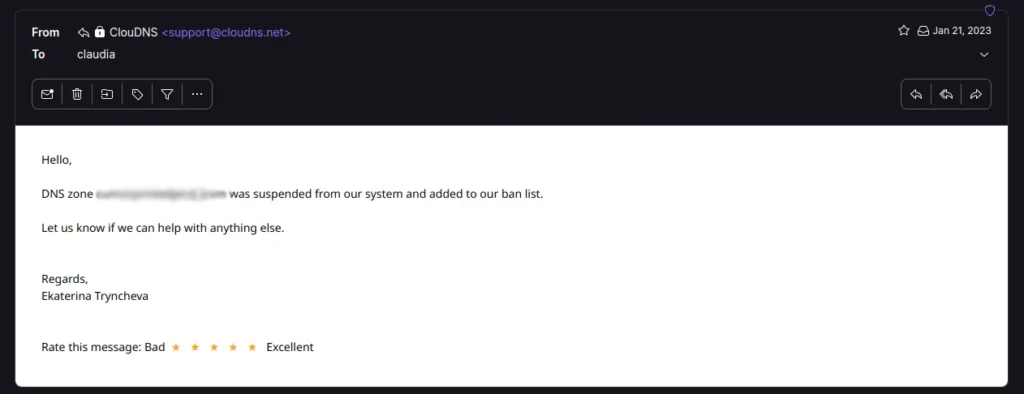
This is an example of what can be done, a pedophile forum was suspended from a DNS server company, the forum was temporarily down and for some time no one could access it.
tools for collecting data from email domains:
Many websites have emails with custom domains, these domains are related to email companies, such as Gmail, Tutanota Email, Hotmail, Zoho email , etc. and this is a way to collect the domain data
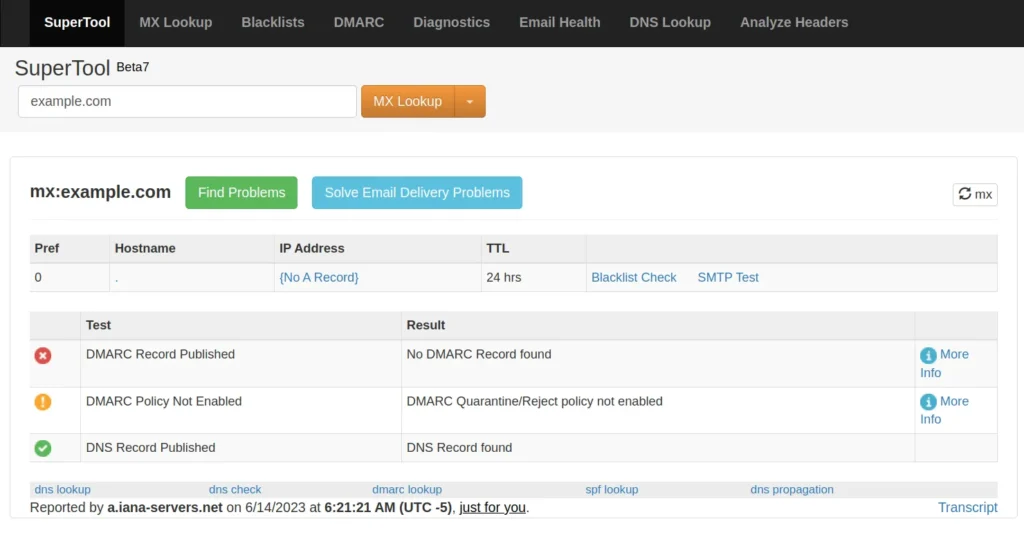
the tool is called supertool and it collects a lot of WHOIS and DNS data, with the MX Lookup. The example.com domain does not have a custom contact domain, so another example will be used with another domain.
This screenshot was created on January 13, 2023, it is a compilation of information and in the hostname it can be seen that the domain of the illegal website uses the email provider called Tutanota Email with a personalized email
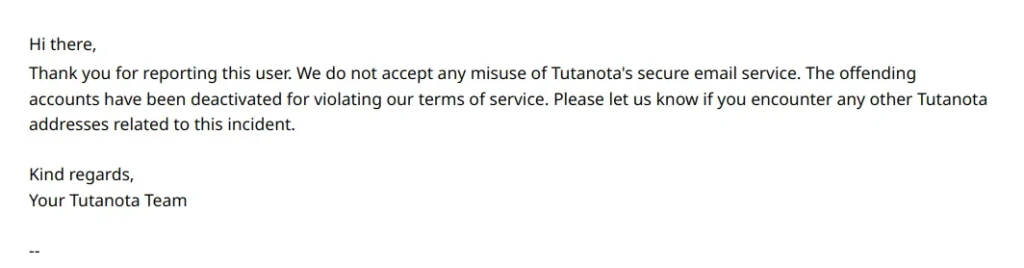
3 days after this data collection, the Tutanota abuse team was notified about a CSAM forum using their infrastructure, and the user’s account was suspended for violating Tutanota Email terms of service.
Many illegal websites have forums, and these forums send verification emails to newly registered. you can ensure that no one can register since many websites send verification codes to emails of the newly registered
Cloudflare and the infrastructure of the website server:
unfortunately the cloudflare service is used by many criminals and even organized crime to hide behind a proxy host, but no service is 100% immune to OSINT and data collection
many illegal websites use the cybersecurity service for protection called Cloudflare, they do this to hide the hosting server from the infrastructure visible to people in whois and IP Address.
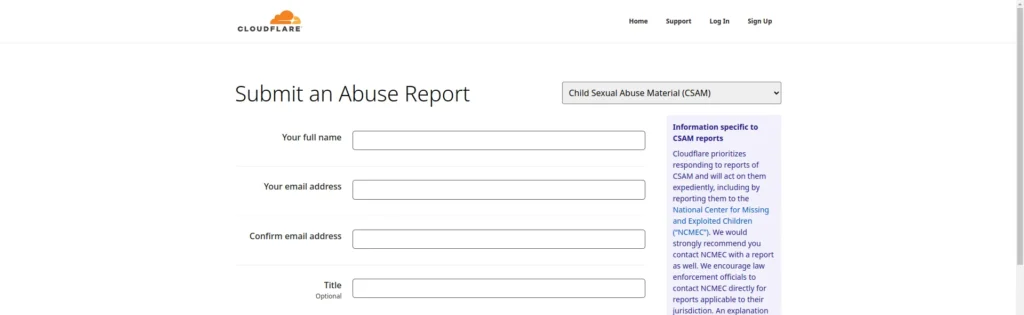
Using the cloudflare service abuse report form, you can obtain information on the illegal porn website that is using the services of cloudflare.
Once the form is completed with your email, in a few hours you will receive a no-replay email from the automatic cloudflare bot with information about the original host and the name of the hosting companys network.
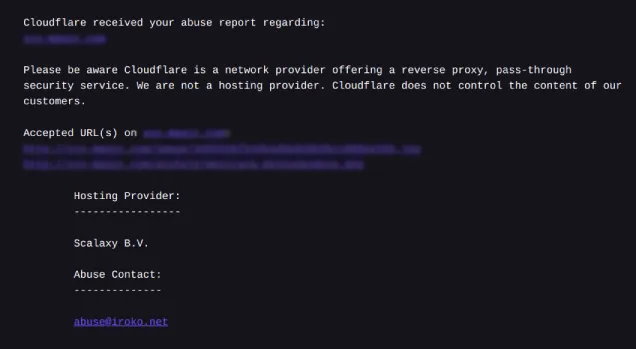
This is a screenshot of an email sent by the Cloudflare Trust & Safety team after reporting Child Sexual Abuse Material on a suspicious website a few months ago. and the child exploitation material was removed
In the report of abuse to cloudflare, the information will also be sent to the organization called NCMEC (National Center for Missing and Exploited Children) and to the authorities
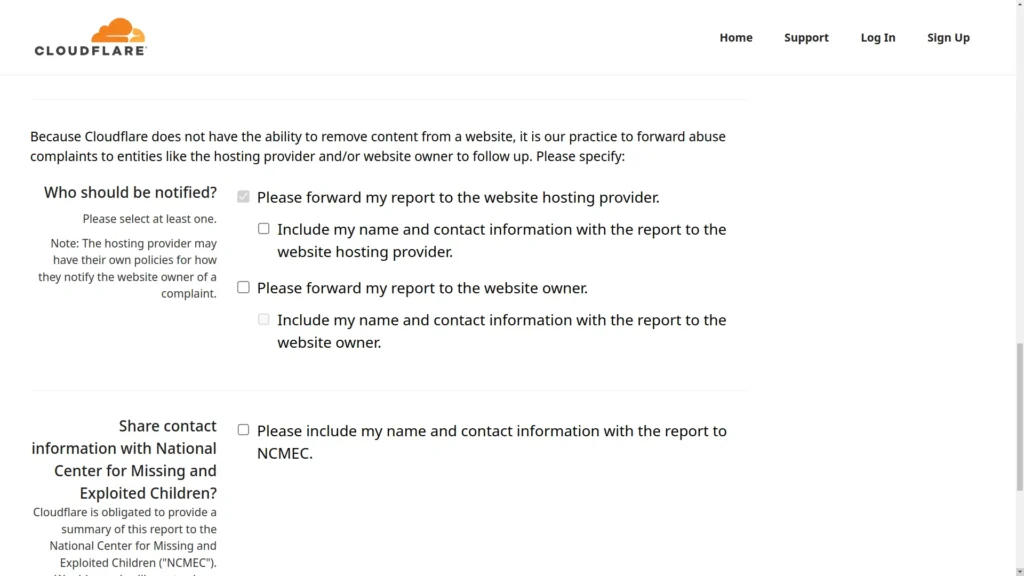
I only recommend sending the information to the hosting provider, do not select more options than the default one.
I do not recommend selecting the option that sends your information and the report to the owner of the illegal website for obvious reasons.
collect information from porn website monetization services:
suspicious or illegal porn websites use ad services to earn money, with this pedophiles and perverts who distribute non-consensual porn earn money and finance organized crime and its illegal activities.
Exoclick fights against organized crime and does not want to be associated with these people, so if you send them information about an illegal porn site that uses the Exoclick , they will suspend all services.
Websites that use Exoclick monetization service use the following URLs and scripts on their websites, which means that seeing this is a way of verifying that a website uses Exoclick service.
Domains list:
1. a.realsrv.com/ads.js
2. syndication.realsrv.com
3. syndication.exdynsrv.com
4. a.exdynsrv.comOne way to check if these domains are active on an illegal porn website is by checking the URLs that appear when you click on an ad or unannounced pop-up window. also checking incoming browser connections.
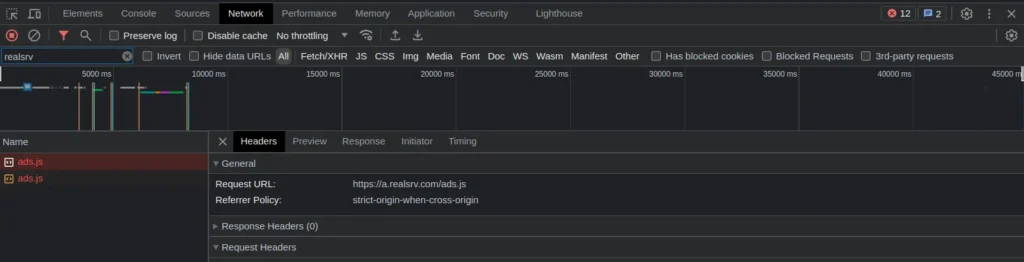
Using the browser by pressing F12 in the network section you can search for the domain or words related to the exoclick service, then restart the suspicious website and analyze the connections.

Another way to verify the existence of the exoclick service on a suspicious website is to go to the source code of the suspicious website.
In a few cases, you can find information about verification codes related to the paid services used by the porn website.
Github repository with ad provider domains and detections:
On Github there is a repository where you can find all the hidden domains of ad providers, and some tutorials to find these domains on internet.
- repository: Advertisements abuse report— Github
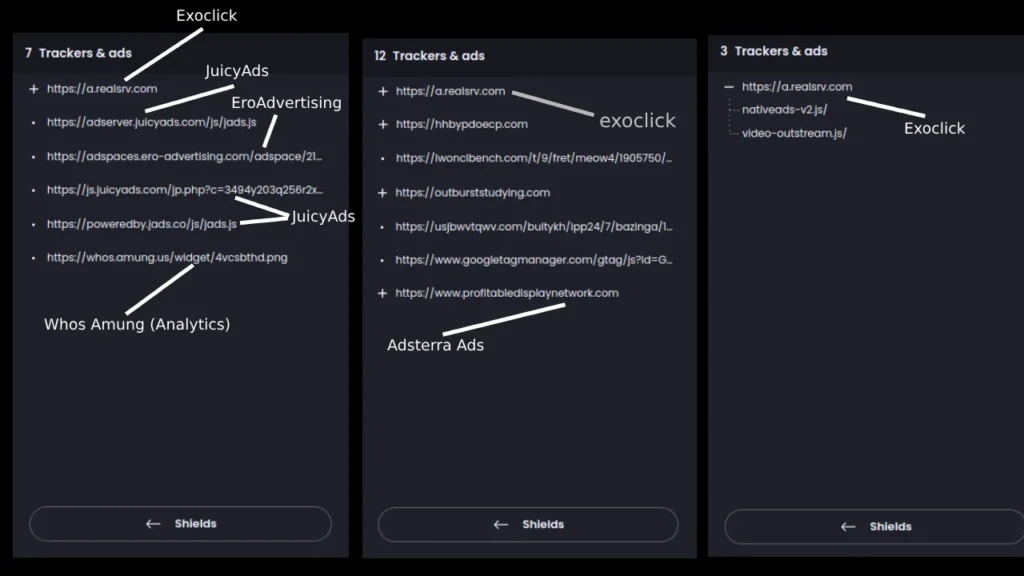
In that github repository you can find many ad provider domains and their email or contact form, also a tutorial on how to detect all this.
OSINT and History of IP Addresses:
but there are tools to view the IP address log history linked to a specific website, this can be useful to gather information and find the server.
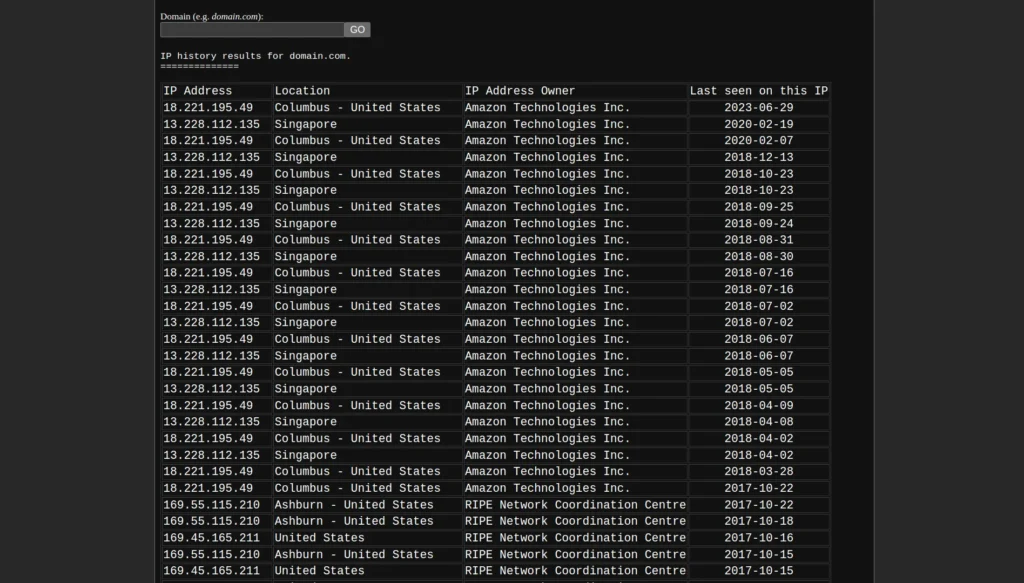
As you can see here, the domain “domain.com” changes its IP address from time to time and since 2017 it has been using Amazon servers, prior to this, RIPE Network records are seen.
These records are from 2012 to 2023, it seems that the domain domain.com has been active since 2012, the viewdns.info tool can be useful to investigate the IP addresses of a domain.
- ViewDNS: viewdns.info