This article is an operation where we revealed the identity of a criminal who owned a child porn and revenge porn website. Nowadays website ceased to exist and it seems that the pedophile thought that he was going to go unpunished
The criminal is a pedophile named Johan Jose Rodriguez Moran who operated 2 child pornography websites from Venezuela. She has been doing this since 2020 and benefited from Child Sexual Abuse Material (CSAM) and pedophilia
beginning of the investigation:
Johan Rodriguez operated a site named selafollan.com that in November 2023, according to semrush, had more than 431k in traffic in November 2023. The pedophile also owned a website named reyespacks.com with over 100k in traffic per month. on these 2 websites Johan made money from illegal content
The users who visited the website were consumers of child porn and revenge porn. Thousands of pedophiles between 2020 and the end of 2023 consumed illegal content. Johan Rodriguez benefited from this monetarily.
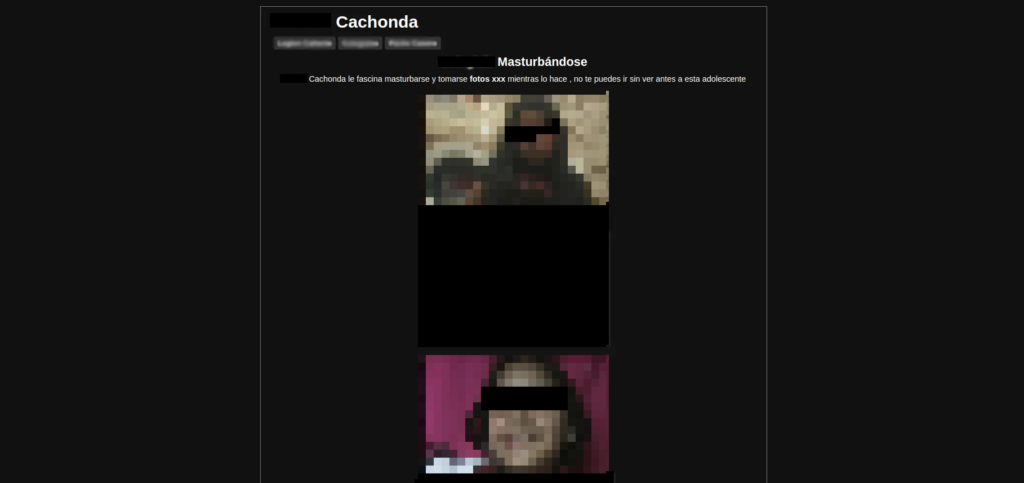
Johan Rodriguez on the website reyespacks.com created in 2021 was dedicated to distributing child exploitation material of girls no older than 12 years old, he used tags such as “little girl” and “schoolgirl” to attract pedophiles.
The pedophile behind the website was dedicated to distributing child sexual abuse material (CSAM) blatantly and without hiding it on his website called “reyespacks” from 2021 to the end of 2023.

In 2020, the pedophile created the website “selafollan.com”, this was Johan Rodriguez’s first website where he began to upload child pornography, revenge porn and content stolen from monthly payment sites such as OnlyFans.
On this website you could say that it is worse than the one created in 2021, it seems to be the same illegal content but with more obvious titles referring to what is child sexual abuse material (CSAM) and revenge porn.

Johan Jose Rodriguez Moran distributed child pornography of children between 12 and 17 years old on these 2 websites. This pedophile benefited from child exploitation and pedophilia for 3 years.
The pedophile has no empathy with the victims of child exploitation, he used these 2 websites for the distribution of child pornography and other pedophile consumers of Child Sexual Abuse Material (CSAM).
Victims of child exploitation:
The victims of child exploitation mostly appear to be from South America, Johan Rodriguez wrote the first and last names of the victims next to photos of the victims’ relatives and social networks of the victims
The pedophile behind the website not only distributed child pornography, he also doxxed victims of Child Sexual Abuse Material (CSAM) by endangering victims and making public information about the victims’ families.

This post was an example of this, a girl who is clearly seen to be underage and the pedophile without any empathy or remorse posts the image, face and caption adds the name of the child sexual abuse material victim
The pedophile used file hosting providers as mega.nz to upload the illegal content. mega.nz is a platform that in the past was used by thousands of pedophiles and pedophile rings for the distribution of child pornography
- abuse report: [email protected] (more information)
The pedophile was suspended from mega.nz for distribution of child pornography, this mind map is a demonstration of how the pedophile with the user “esgalactico” distributed child pornography in “reyespacks” and mega.nz

The pedophile on the website “reyespacks.com” in addition to uploading child exploitation material, name of the victim and photos of relatives. Johan Rodriguez also uploaded photos of young family members of the victim of child exploitation. A girl no older than 6 years old next to the other victim of child exploitation.
On these 2 websites, another non-consensual pornography and child pornography website was promoted. The admin of these websites posts illegal content there also under the username “Esgalactico”.

the name of the account “Johan Rodriguez” and it was manually verified by the administrator of that shady website that is promoted by pedophile.
The pedophile uploaded child pornography with download links to this website. On November 4, 2023, he uploaded illegal content with his first and last name
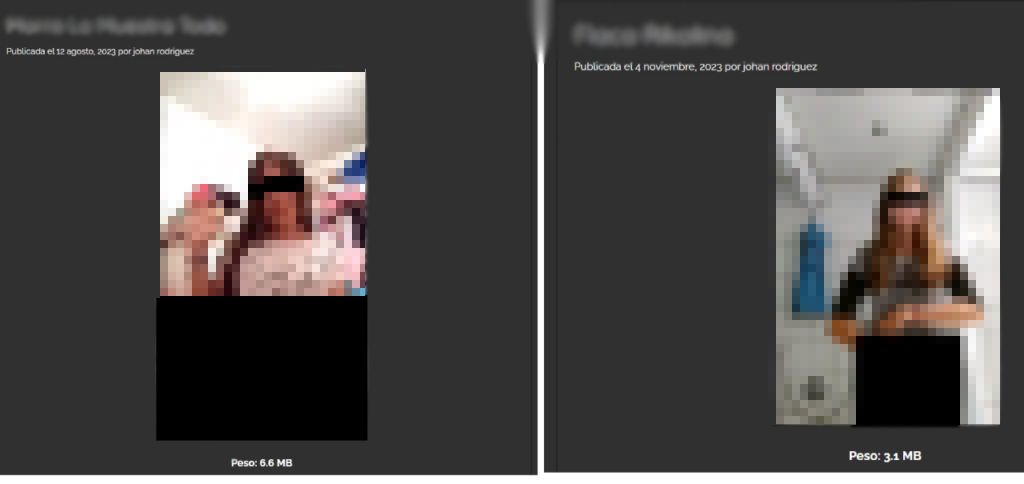
The pedophile using the nickname “Esgalactico” and “Johan Rodríguez” distributed a lot of child pornography, the pedophile profited from child exploitation and the suffering of many children.
Investigating the pedophile behind the website:
Now let’s find out who’s behind reyespacks.com and Selafollan.com Let’s see who is behind the illegal activities that affect the most defenseless.
The first thing we are going to look at is the WHOIS records of the 2 domains, in these records you can see how the pedophile uses privacy whois to hide his identity but still WHOIS reveals useful information

In these WHOIS records it was possible to collect that the owner of the 2 websites is from the country Venezuela and lives in the state of Miranda.
In a reyespacks section there is a page where the pedophile owner of the website shares links to Telegram groups and Twitter accounts he owns.

the pedophile had a telegram group called “Dioses Del Porno” in Spanish. The link of the Telegram group coniside with the sale of the property of the Telegram group with the same name. the auction on ForoBeta.
On the Telegram group seller’s account you can see a profile picture, the name “Johan” as part of a username, and other useful information such as that the account was verified with a phone number registered with Wahtsapp
Using the SEON tool, search for the ForoBeta username by joining the “@gmail.com” to verify the existence of a Gmail email account with the username [email protected] which is the same as the one registered in ForoBeta
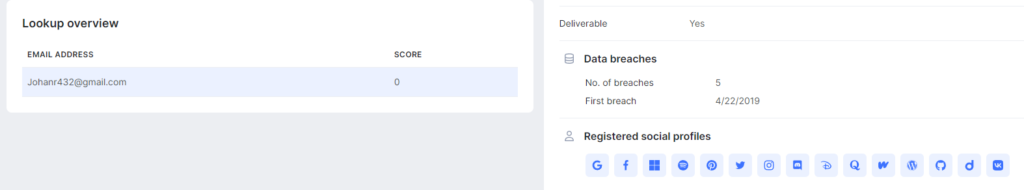
the email address did reside with a Google / Gmail account and was registered on many social networks. so to see more detailed social media logs I used the OSINT INDUSTRIES tool when it was free to access.

the results of OSINT INDUSTRIES displayed usernames and social media account information linked to the email, in Gravatar’s account Johan uses the name “esgalactico” as the administrator user of reyespacks.com
The Google account linked to Gmail was created more than 9 years ago according to the records of Johan Rodríguez’s Youtube channel.

On Johan Rodríguez’s YouTube channel there are some videos that appear to be for the university where he attends in Venezuela. Useful metadata such as Johan Rodríguez’s identity card number (26210647) appear in the videos
The last video uploaded by Johan is about the fifth installment of a work for the university, in which we can see different numbers in the title of the video.

The Peruvian National Police uploaded a tool for the verification and obtaining of information on identity cards of civilians in Venezuela. this using the public database of Venezuela’s national electoral registry
When I wrote the numbers that are written in the title of the Youtube video in this OSINT tool of the Peruvian police, I found that exactly the numbers matched the identity card of a Venezuelan citizen of the same name as the pedophile.

the pedophile’s full name is “Johan Jose Rodriguez Moran” and he is from the state of Miranda. Other website owner information can also be found such as location information where he will vote in the election.
Now going back to the information provided by the OSINT INDUSTRIES tool, let’s get into the gravatar website and the username “esgalactico” which is the one that Johan Rodriguez uses as an admin in reyespacks.com

In the information in JSON format we can see how in the gravatar account information the first and last name (Johan Rodríguez), the username and a link to a website with a free WordPress subdomain can be collected
When you go to the website hosted on a subdomain of wordpress.com it looks like a beta of what “selafollan.com” was and this coincides with the creation dates of the domain and this subdomain.

On the wordpress.com-based website, the pedophile distributed non-consensual or revenge pornography using words like “leaked.” There are 3 posts from 3 different victims of non-consensual pornography on the website.
Among the victims are a military man from an unknown country and a girl who is categorized as an “adolescent” by the pedophile. Hispanic pedophile networks refer to this word to refer to minors.
In the posts uploaded to the website in the final section it shows how the user “esgalactico” is the user who posted it, who also liked himself and this revealed the profile of Gravatar is the same as the one seen before on OSINT INDUSTRIES
The name “esgalactico” is also used by a Pastebin account. This account published a post where it references the domain “selafollan.com” and links to download hosted on Mediafire and mega.nz
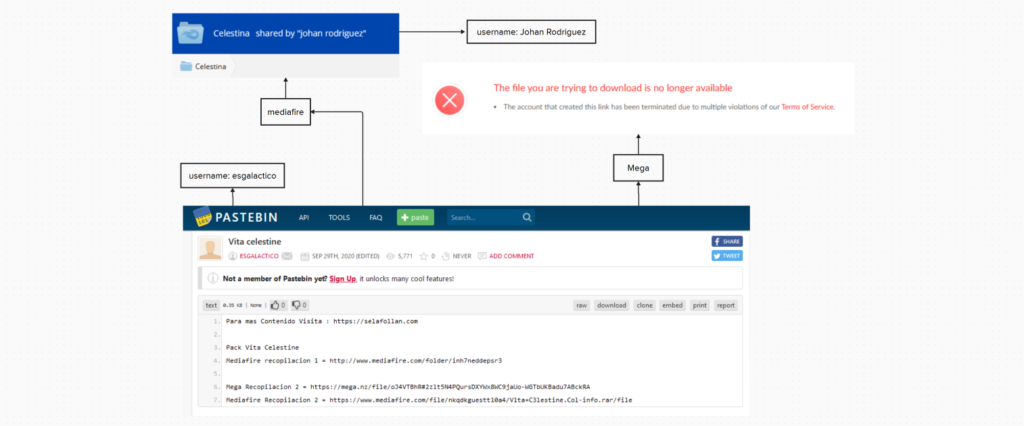
On the Mediafire account that uploaded a file folder, the username that was used by the account owner is “Johan Rodriguez”. The same first and last name of the owner of the email address [email protected]
The mega.nz account was suspended for “multiple violations” of mega.nz according to the file hosting provider. based on Johan’s history of illegal activities, it is likely that he used the account to distribute CSAM
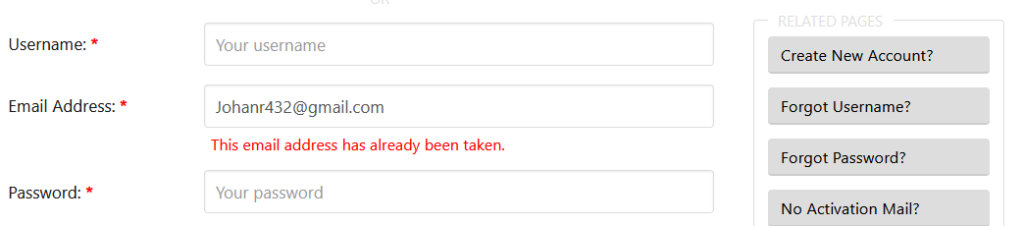
The email address is [email protected] registered to a Pastebin account. The email address is being used by a user and for that reason it is not possible to register an account with that email address.
Going back to the JSON records provided by OSINT INDUSTRIES, in the JSON records they appear as the Gmail address is registered in xvideos and xnxx.
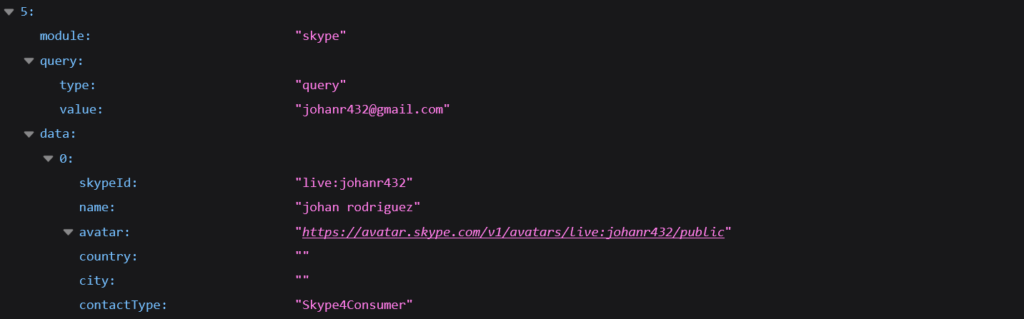
also the email address is linked to a Skype account that has the username “Johanr432” and the first and last name “Johan Rodriguez. The Skype account profile picture is the default Skype photo
Johan Jose Rodriguez Moran is registered on document upload websites. these document websites are Studocu, Scribd, and docsity. Johan uses them to upload university-related documents. There’s a lot of information here

the PDF files uploaded by Johan Rodriguez on these websites are documents related to the university where the pedophile attends.
the name of the university in which Johan Rodriguez is called Instituto Universitario Politécnico Santiago Mariño (PSM) in the Caracas state.

the owner of the account is Johan Rodriguez, he has the same profile picture as his Google account linked to the Gmail mentioned above. the pedophile uploaded 2 documents to the website called Studocu.
in the intro of the document, Johan Rodríguez’s identity card is mentioned. it is exactly the same as the identity card (DNI) mentioned on the Youtube channel.

The university named “Politécnico Santiago Mariño” (PSM) is the university that Johan Rodríguez attends or attended. The university is in Caracas, Venezuela.

From what can be seen in the documents and videos uploaded by Johan Jose Rodríguez Moran, the pedophile studies hardware computing, programming and creating software to control hardware.
The university is a private university where students pay $50 per month to access learning at the university. According to one theory, it is possible that the pedophile got the money from these aforementioned illegal activities.
In 2017, Johan Rodriguez attended a high school. This institution uploaded the high school database to its GitHub. That database mentions Johan Rodríguez’s email address, username and location according to 2017 records.
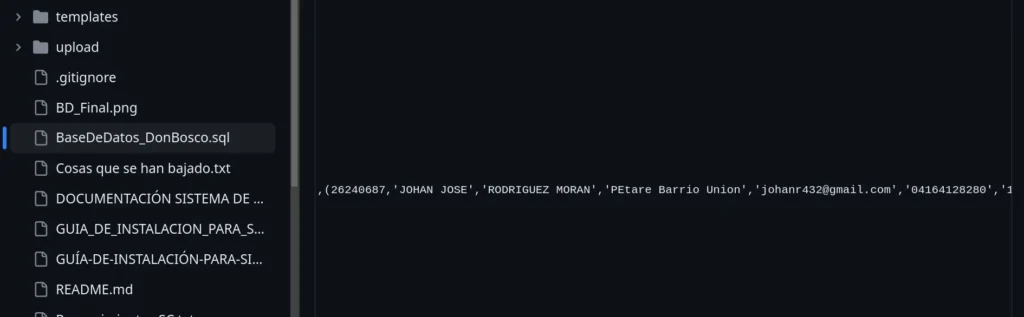
The GitHub repository was uploaded 7 years ago. in the SQL file is the above-mentioned information of the pedophile. which is consistent with all the information previously mentioned in this article.
Now that we know enough information about the pedophile who owns reyespacks.com and selafollan.com, let’s investigate his social networks. there is a Facebook profile owned by the sexual depredator and pedophile.
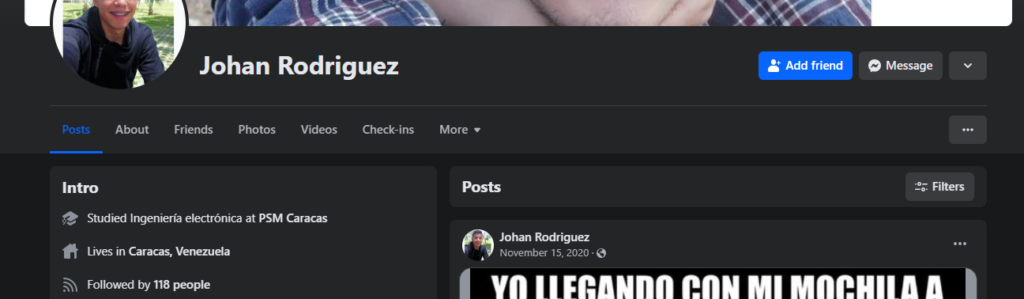
The last public publication of the pedophile was on November 15, 2020. the information in the profile shows that he studied at the PSM Caracas and that he currently lives in the town of Caracas, Venezuela.
The username of the Facebook account is “johanr432” which matches the username of the gmail address used by him to manage profiles of Pastebin, xvideos, Gravatar, WordPress and among other social networks and websites.
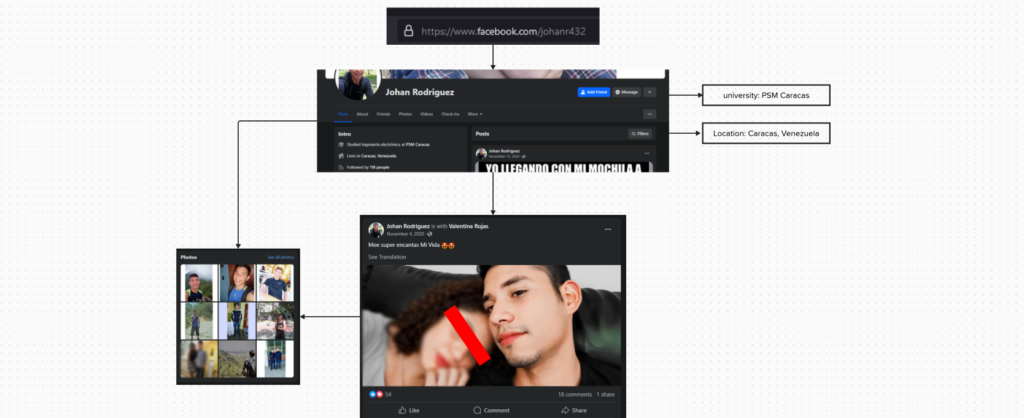
The pedophile named Johan Rodriguez uploaded a photo with his girlfriend on Facebook. This photo was uploaded in 2020 and the pedophile’s face looks a lot like the profile picture used on the website named ForoBeta.
In a post where Johan Rodriguez was tagged on Facebook, a photo with the pedophile and the father is shown in the same photo uploaded to Facebook.
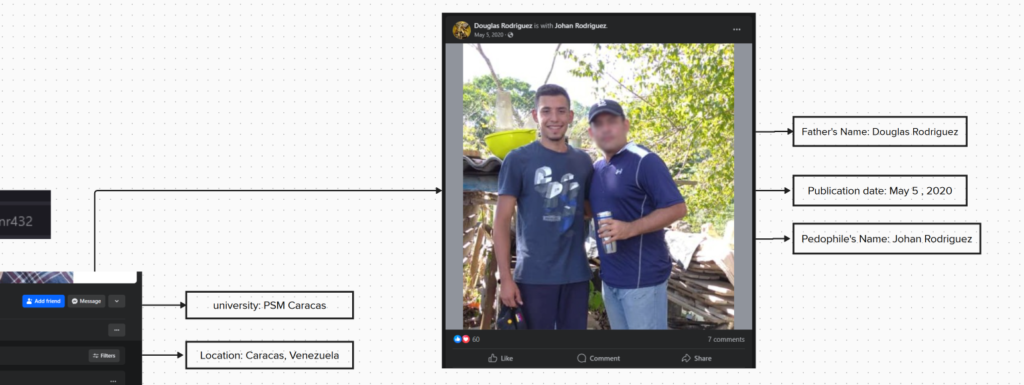
the pedophile’s father is named Douglas Rodríguez. A religious person who has 2 children and one of them is the pedophile who owns reyespacks.com.
The pedophile’s best friend is called “Jesús Bastidas”, these 2 people seem to be very close and the last public photo registered in Johan Rodríguez (the pedophile) is on Jesús Bastidas’ instagram profile.
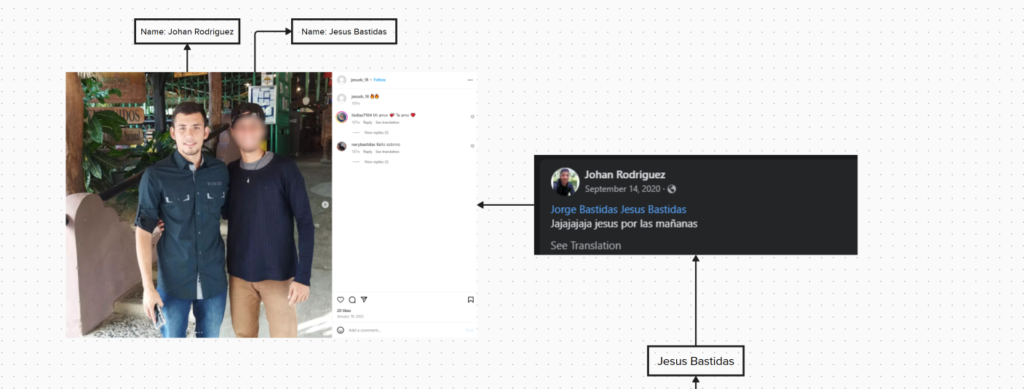
From 2020 onwards, Johan Rodríguez began to be more anonymous and left public social networks aside. This co-exists with the creation of reyespacks.com and selafollan.com. Public inactivity is likely due to illegal activities

Whenever people think of a pedophile, they imagine someone very adult, dangerous, dark, ugly, without friends and family and etc. But in truth pedophiles look like that. They may have the face of a normal person with no bad intentions, but inside they are very dark people.
the cover or banner of Johan Rodriguez’s Facebook account shows a child hugging Johan Rodriguez. while he had that photo for 3 years he distributed Child Sexual Abuse Material (CSAM) and profited from child exploitation.
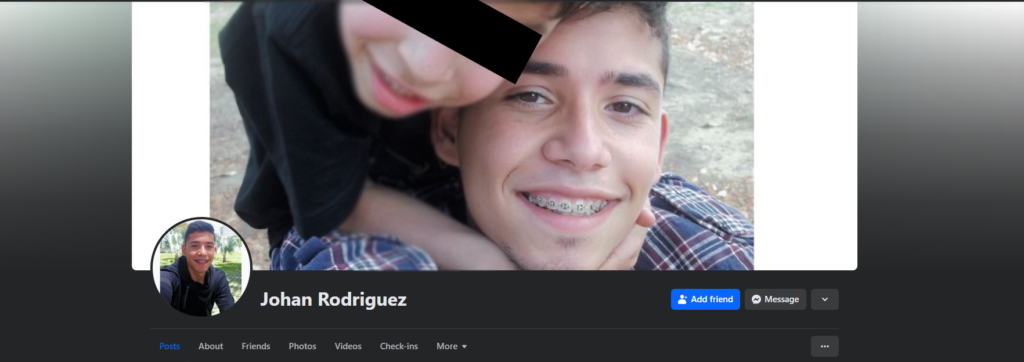
that photo uploaded by Johan Jose Rodriguez in 2018. until now that I write this (2024) he still has this cover photo on the Facebook account. Many times the least thought-out people are the most evil.
Hackers and LinkedIn accounts:
Johan Rodriguez while managing 2 wen child exploitation sites was also registered on hacker forums and on suspicion of hacking-related activities.
On a hacker forum called nodo313, the pedophile was registered and posted a single thread where he asked hackers for cracked Linkedin accounts. Users of the hacker forum questioned the pedophile about why he wanted the accounts
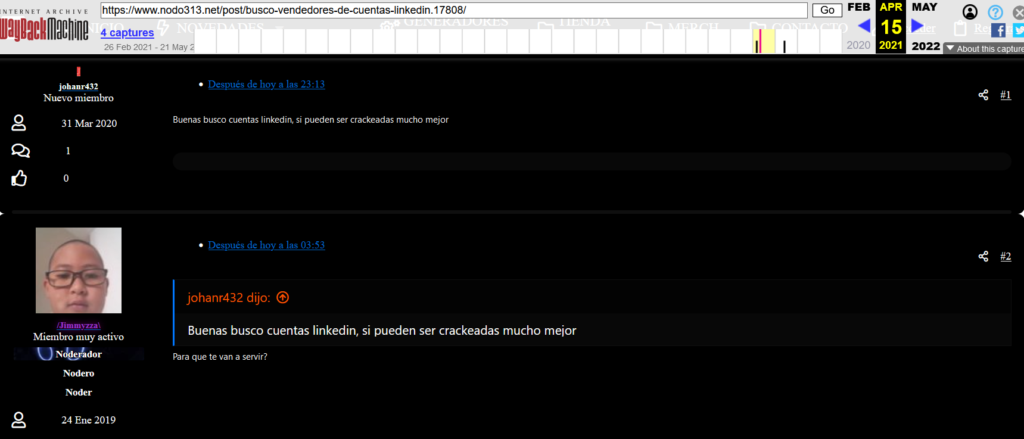
Johan Rodriguez was looking for a Linkedin account owned by a real person who has been hacked for currently unknown reasons. Suspected for Identity Theft
Johan Rodriguez in Facebook groups on October 2, 2019 was asking for help for the creation of multiple Linkedin accounts a day. He explains how he used VPNs to avoid being detected by LinkedIn’s system.
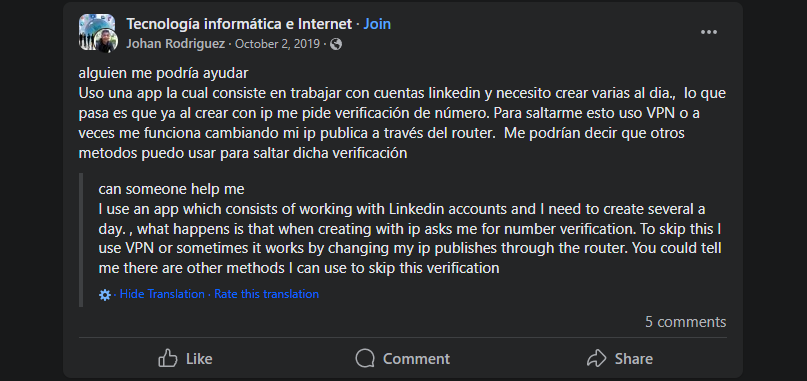
Johan Rodriguez was interested in the creation of fake Linkedin accounts from 2019 to 2021 according to these records. The reasons for this are unknown.
The pedophile on his Facebook account shared the link to an “ethical hacking” group created on Facebook. This hacking group has 11k members as I write this. it seems that Johan Rodriguez likes this type of activity very much.
As a curiosity, the pedophile on his Facebook profile shared a post in the form of a meme that refers to a meme that refers to his family being happy because the pedophile managed to make a living from programming.

It is very likely that the pedophile will say that he makes money thanks to “programming” so as not to tell his family where the money that the Johan Rodriguez earns on the Internet really comes from
Upon digging deeper into this, I discovered that Johan Rodriguez owns a Linkedin account named “Ximena Yaquin,” a made-up name. in the description of the account he claims to be a student of PSM (University of Venezuela).
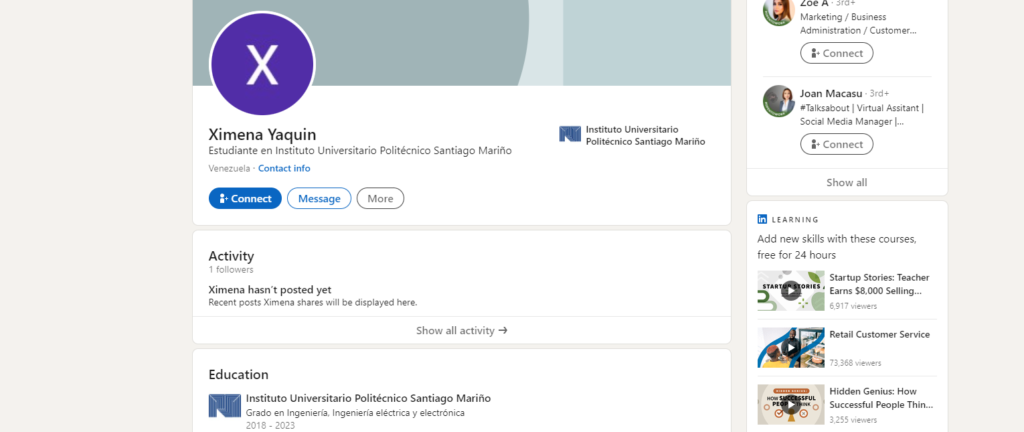
In the contact information of the Linkedin account you will find the account link next to the website link “selafollan.com”. this account is owned by the pedophile named Johan Rodriguez. “Ximena Yaquin” does not exist.
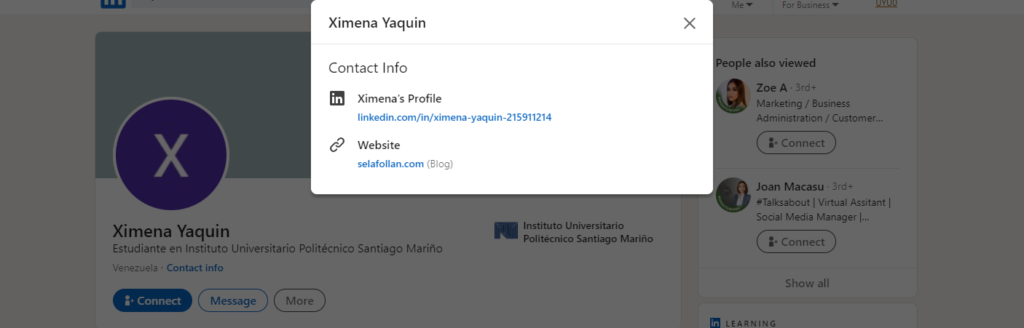
In the “Education” section of the LinkedIn account, the name of the university is displayed next to the years of education. He started university in Venezuela in 2018 and finished his studies in 2023
Telegram groups with illegal activities:
In this article, it was mentioned earlier that Johan Rodriguez owned telegram groups. In this section we will focus on the Telegram groups owned by the pedophile and look at the illegal activities on Telegram as well
The website reyespacks.com had a Telegram group, in that Telegram group images of minors and child exploitation material were distributed and the original publication link on the illegal website called ReyesPacks
After Johan Rodriguez sold the telegram group “Dioses Del Porno” on Forobeta, he created another illegal telegram group with the exact same name and where he uploaded child pornography and photos of children.

This Telegram group has more than 3 thousand members who are pedophile consumers of Child Sexual Abuse Material (CSAM). The original group that was sold to someone anonymous had over 15k members.
The posts of the telegram group coinside with a post published by Johan Rodriguez on an illegal website in the same month that the same illegal content was published in the telegram group called “Dioses Del Porno”.
In addition to these 2 telegram groups, the pedophile manages another group called “selafollan” where Johan Rodriguez does exactly the same as in the other 2 telegram groups with Child Sexual Abuse Material (CSAM).
This Telegram group has more than 1k members. The pedophile named Johan Rodriguez owns a network of illegal telegram groups, between all the groups they form more than 6k of pedophiles consuming child exploitation material.
Sexual predators who consume child pornography after a while of joining are suspended from Telegram. They are very likely to be suspended from Telegram for distribution of child pornography and other illegal activities.
Other useful information from Johan Rodríguez:
Here I will mention other information that may be useful regarding this research. for example, the pedophile’s personal phone number and PayPal is linked to a Forobeta account. Account was created on December 12, 2019

when the pedophile sold the telegram group with 15k members on Foro Beta, he accepted Binance Pay, Bitcoin, and ForoBeta as a form of payment. It is likely that the Telegram group was paid for with cryptocurrency.
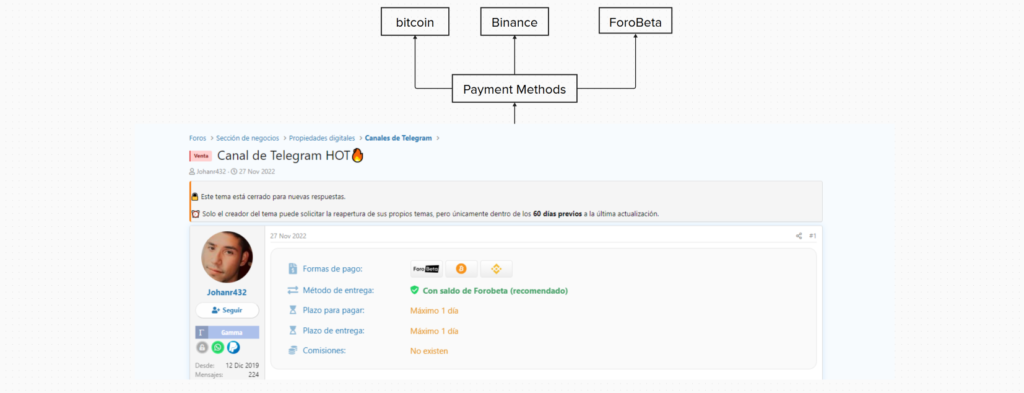
In another post by the pedophile, he put 3 Twitter accounts up for sale. the payment methods that Johan Rodriguez accepted were Binance Pay, Bitcoin and PayPal. He allegedly sold them at the price of $1.
He posed as porn actresses and OnlyFans users on Twitter. He made them think he was a girl and thousands of people started following him. Johan Rodriguez made a business model out of this. Basically with spoofing.
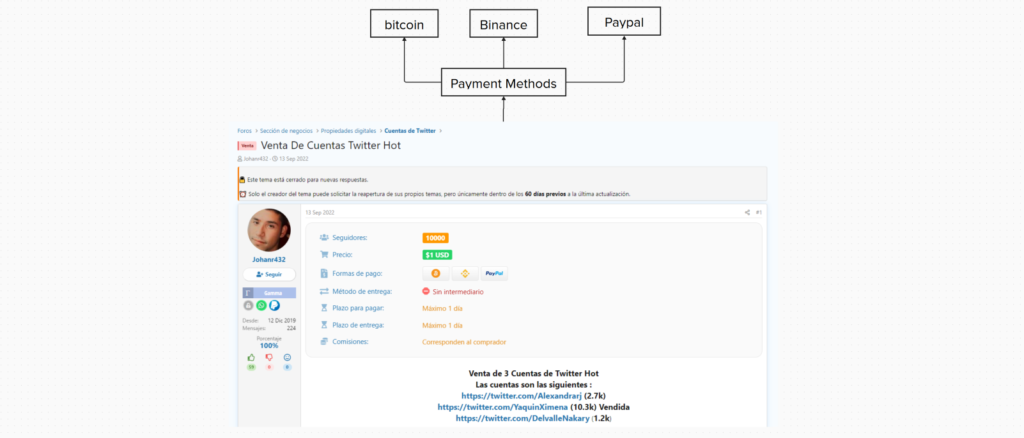
He managed to sell an account with more than 16k followers on Forobeta. but apparently 2 of those 3 accounts mentioned by Johan are still owned by him, and he continues to impersonate a woman on twitter to gain followers.

In another post, he sold a Facebook page with 34 thousand followers, he sold this page at the price of $30. For a while she posed as a very famous Tik Tok user but on Facebook to gain followers. Basically, spoofing again.
In a comment response from Johan Rodriguez, he thanks an offshore hosting provider and said that he moved his website to the offshore hosting. Offshore hosting is used by criminals to evade the law and authorities.
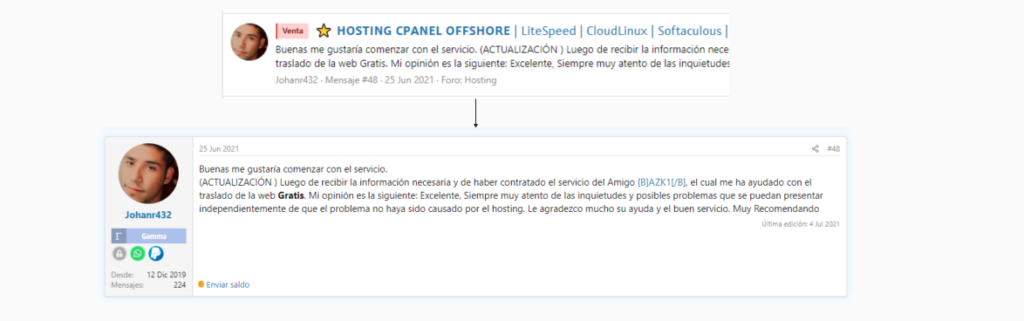
Offshore hosting is used by criminals and criminal networks to store websites on servers far away from the country where the criminal operates. In countries generally with few laws regarding the Internet.
Johan Rodriguez’s exoclick account was suspended for violating exoclick’s compliance policies. he complained about this on ForoBeta. That means reyespacks.com and selafollan.com were using ExoClick

on the website Forobeta the pedophile was complaining about this. It didn’t fix the problem and started trying to find a new ad provider. although it seems that he was not convinced by any ad provider.
In another post on ForoBeta, the pedophile thanked a user of the website who made a thread about websites to promote URLs and thus get traffic on websites. Reddit and medium.com are mentioned in the list.
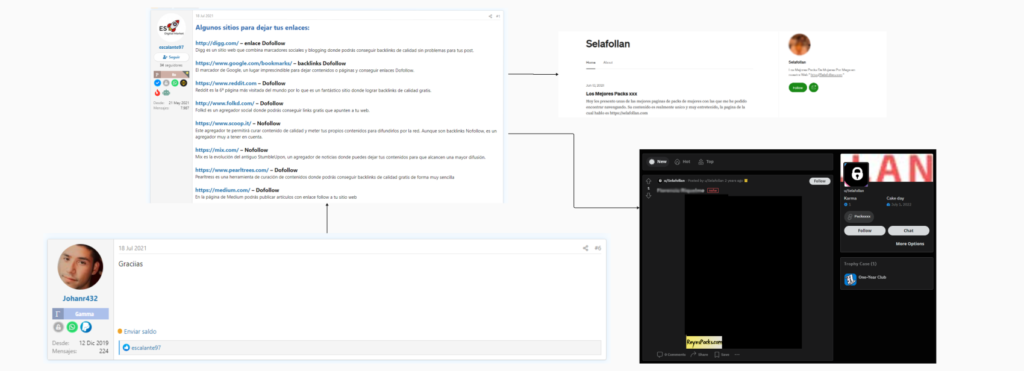
On Medium he wrote an article promoting the website “selafollan.com”, on Reddit the pedophile posted adult content previously published from reyespacks.com. In the account description there is a link to selafollan.com
Information on data breaches:
By using OSINT methods to access public databases, people can get a lot of information. the SEON tool provided us with a list of 5 security breaches found. Here we will delve deeper into the public information found.
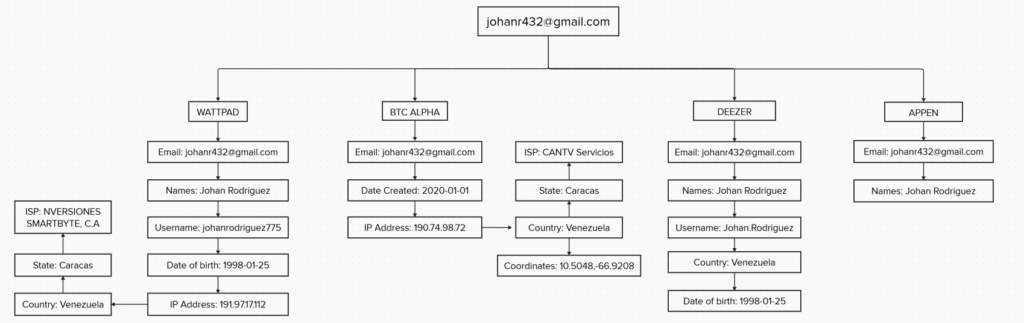
Using OSINT tools to access databases that suffered data breaches we were able to find usernames, date of birth, IP addresses and locations of the pedophile owner of the telegram groups and 2 child exploitation websites.
with the information from the data breaches we were able to find Johan Jose Rodriguez Moran date of birth mentioned 2 times. He was born on January 25, 1998 and at the time of writing this he is 26 years old
Johan Rodriguez started and registered his first website in the year 2020. Which means he began at age 22 to profit from child porn and non-consensual porn.

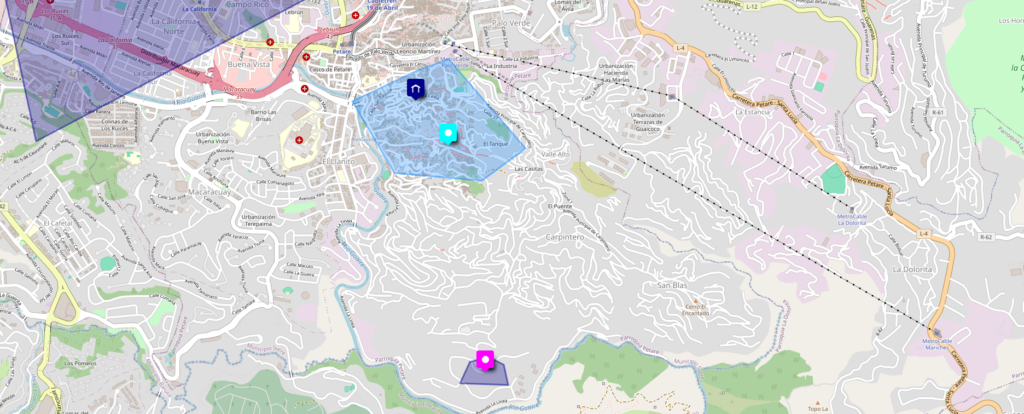
using the IPinfo.io tool we can see information about the pedophile’s IPv4 address. The 2 IPv4 addresses are in the Federal District of Caracas in Venezuela. They seem to be in the same state and in the same city in Venezuela.
IPv4 and IPv6 addresses in many cases do not tell the exact location. but by triangulating the position using these 2 IPv4 addresses we can obtain more approximate information about the location of the pedophile.

with this information we can know where in Caracas the pedophile is. the red icons and the red triangle are the 2 IPv4 addresses collected above. the 2 IPv4s are in different locations but very close to each other
The blue icons and the blue triangle are the exact locations of the educational institutions where the pedophile studied. With this we discovered that the IPv4 addresses were very close to the pedophile’s actual location
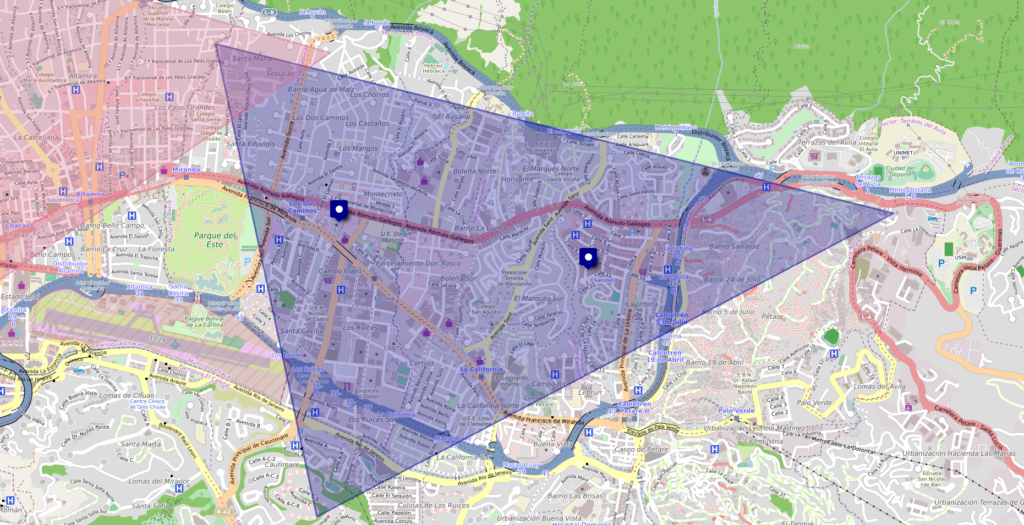
When I researched the area of the state of Caracas where this blue triangle was, I discovered that it was the Miranda area. Miranda is a city that is located in Caracas that we mentioned earlier in the article.
Miranda was mentioned by the WHOIS records of illegal websites and was also mentioned when we investigated the identity card of the pedophile.
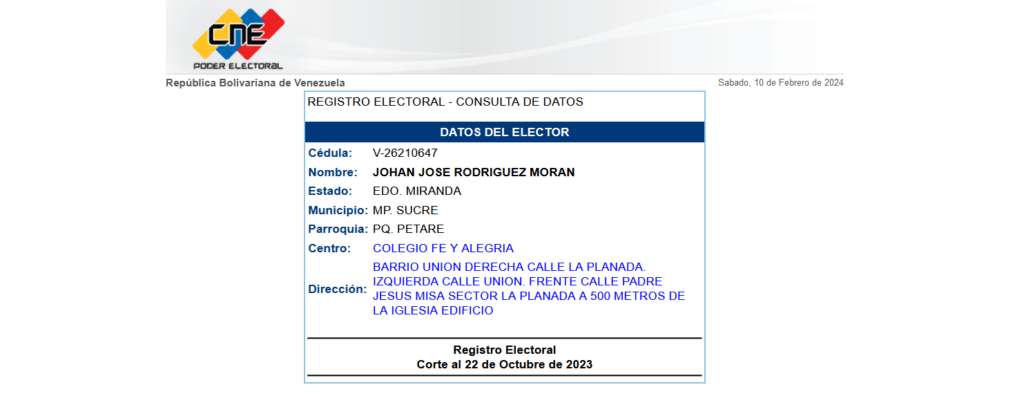
Police in Peru were using an API from Venezuela’s electoral registry website. I figured out how to do it manually and officially by reviewing the logs.
The exact same logs are displayed as with the other tool. But this time I know something I didn’t know before and that is that I wrote down the home address of the pedophile owner of the illegal pornography website.
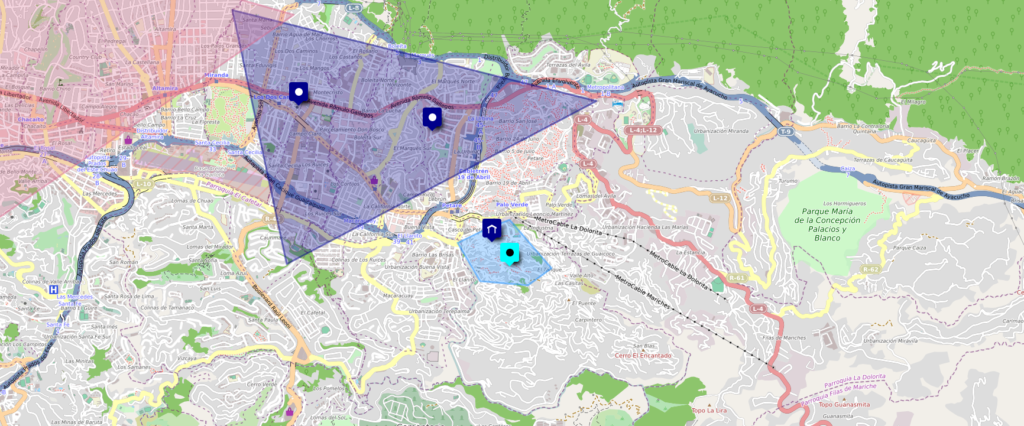
the alleged address of the pedophile according to the public electoral registry is located in Barrio union, Petare, Miranda, Caracas, Venezuela. this location is close to the 2 student centers that Johan Rodriguez previously attended.
According to Venezuela’s Electoral Registry, the pedophile’s house is located on the street named “Calle la Planada” in Miranda. It is a short street so the proximity range of the pedophile’s house is very short and it is the location where the pedophile would operate the child pornography site.
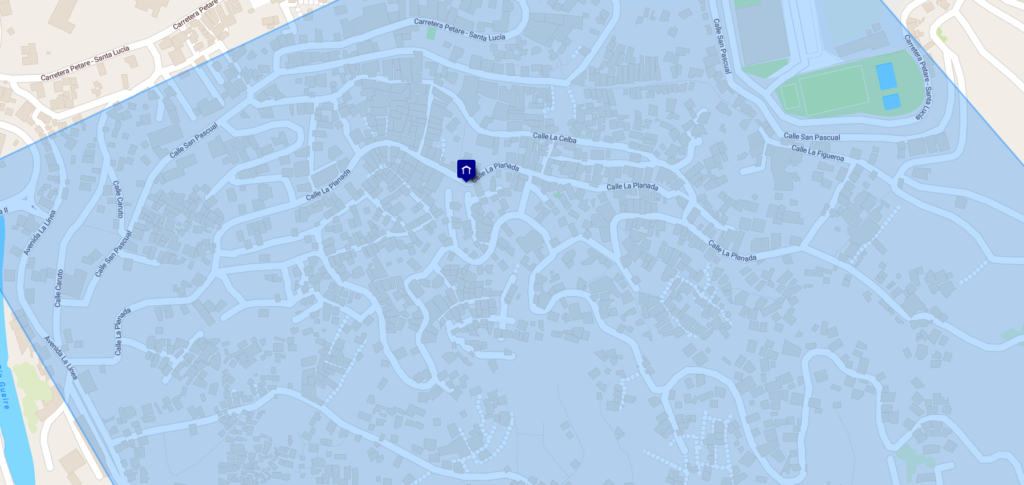
Using geolocation with advanced OSINT methods we can know where the pedophile lived. After all, the information was already public before. We just had to connect enough things to get the result.
According to the registry of the electoral power, the civilian Johan Rodríguez has a location to go to vote in the elections, according to this registry he goes to vote at the Fe y Alegría school. This school is close to where the pedophile lives
The Business of Piracy Websites:
Johan Rodriguez in January 2024, using the domain “reyespacks.com”, hosted a piracy website called “ALLDD” for a few days until he deleted everything again. Prior to this, the domain simply redirected to alldd.net

the website is a copy of Netflix. It is written in Spanish and the domain was purchased and registered on February 8, 2023 at 9 p.m. and was repurchased February 9, 2024. It’s been a few weeks since I’ve been writing this.
With the host.io tool I was able to find more domains that redirected to the all.net domain. Apparently, there are more domains besides reyespacks.com that redirect to all.net. They are mostly piracy websites.
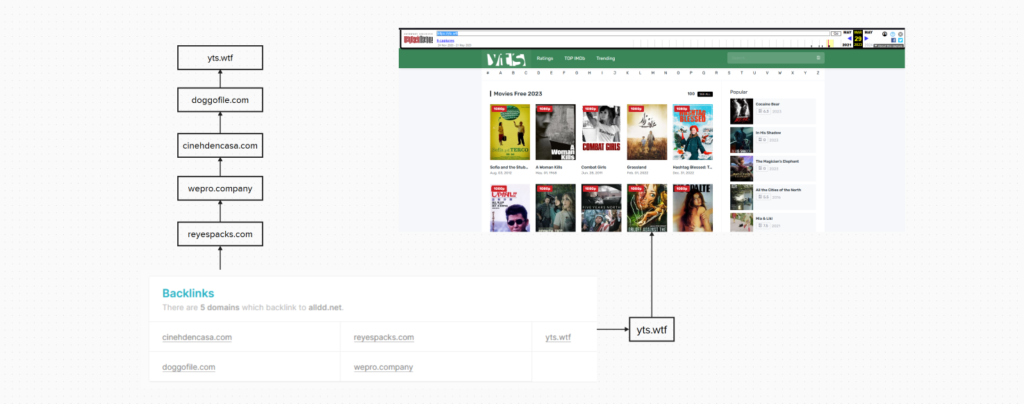
Analyzing the title of the website with the host.io records can see that 3 domains in addition to alldd.net have the title “ALLDD” on the website. so we can verify that these 3 websites are linked to reyespacks.com and alldd.net
These 3 websites are written in Spanish and all 3 use Cloudflare infrastructure. Of these 3 Piracy websites, only 1 is recorded on the Wayback Machine. Currently the 3 websites are down as well as alldd.net.

the only website that does not have the title “ALLDD” is the domain “wepro.company” which is called “DescargasDD”. This website is also inactive but does not have the same name. even so, it carries the “DD” characteristics
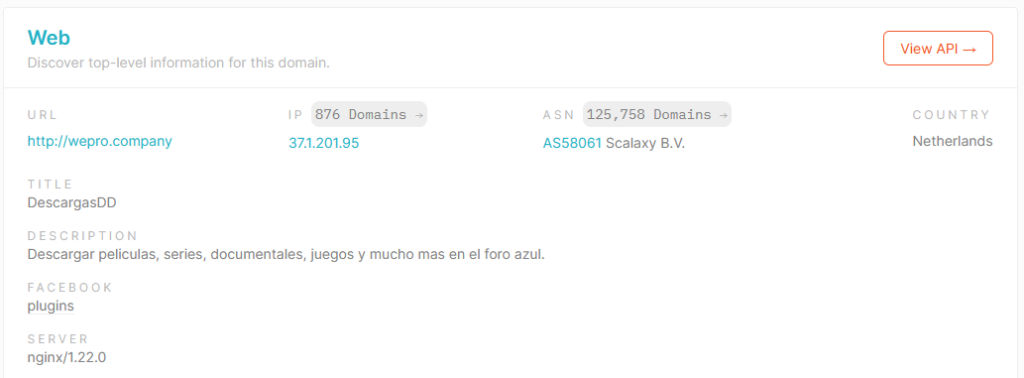
It is likely that this website was intended to masquerade as another website of the same name which is a forum for piracy movies and series. the domain name has the same name as a company named “wepro Company”.
going back to the website alldd.net I could find in the records of archive.org as in the early versions of the domain ALLDD was not a piracy website. the website was about downloading videos from different websites such as Twitter.
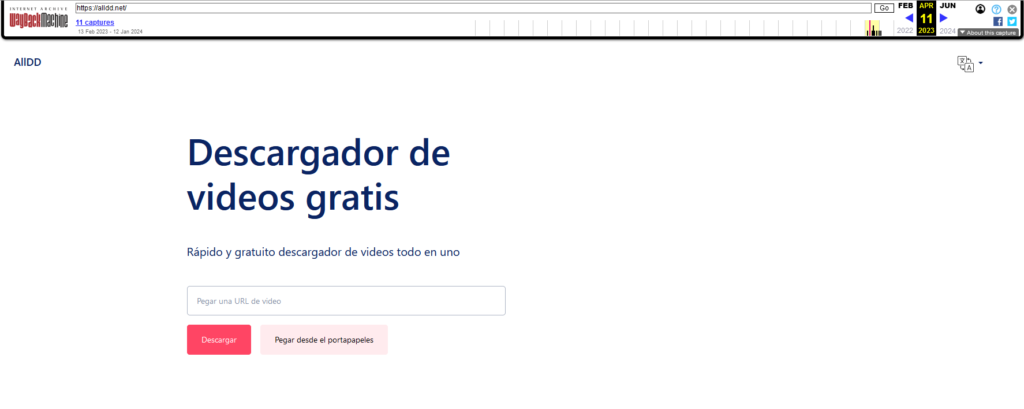
The website is written in Spanish. Only the source code of the video download was hosted for 2 months and then changed to a WordPress theme based on the piracy of series and movies.
Providing Virtual Work on Freelancer Profile
With the name “Esleiter R” and username esleiter7, the pedophile is registered with Freelancer as a website and app programmer. I don’t think the profile picture is the one but it’s possible that he used a very old photo so as not to be located

the account information shows that he is from Caracas, Venezuela and that he charges $3 an hour to program websites. as in ForoBeta he has the phone number, email and Facebook account connected to his Freelancer account.
In Esleiter7’s portfolio he publicly promotes himself as the creator, programmer, wordpress theme designer, website logo creator selafollan.com. He says the website is the best “in its class” He says he charges $3 an hour to offer services.

The profile name is fake. such as Linkedin’s first and last name. It is normal for the pedophile to use nicknames or fake names and surnames on the Internet. This is so as not to be recognized and find their identity.
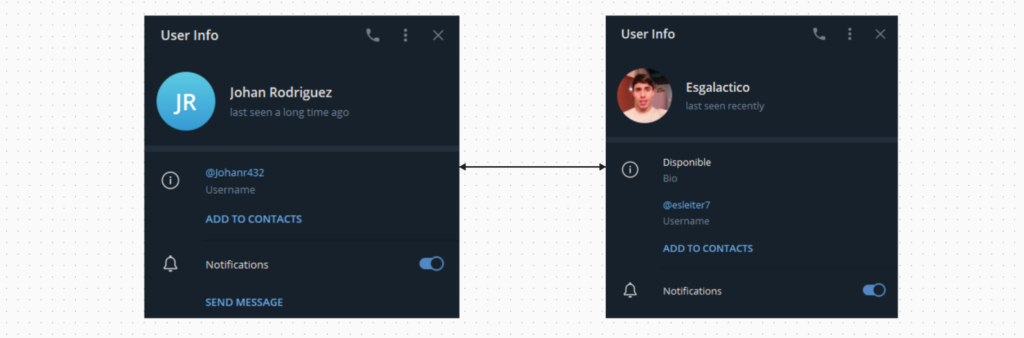
the profile picture coinside with a Telegram account named “esgalactico” as the nickname used by Johan José Rodríguez in reyespacks.com and selafollan.com in addition to using it as a username in the currently suspended WordPress blog
Summary of the research article:
Johan José Rodríguez Morán is a pedophile living in Venezuela. Since 2020 it began distributing child pornography and non-consensual pornography from Selafollan, Reyespacks and a network of Telegram groups.
During 2020 until the end of 2023, in addition to distributing Child Sexual Abuse Material (CSAM) and non-consensual pornography, he published personal information of victims, thus putting victims in physical danger.

He posted personal information about the victims such as first and last names, photos with relatives, social media and phone numbers and images collected from the victims’ social media. putting child victims in extreme danger.
The pedophile has no empathy for anyone. He is an evil and psychopathic person who for 3 years profited from child exploitation and non-consensual porn. He did not hesitate for a second to do this despite consequences to the victims
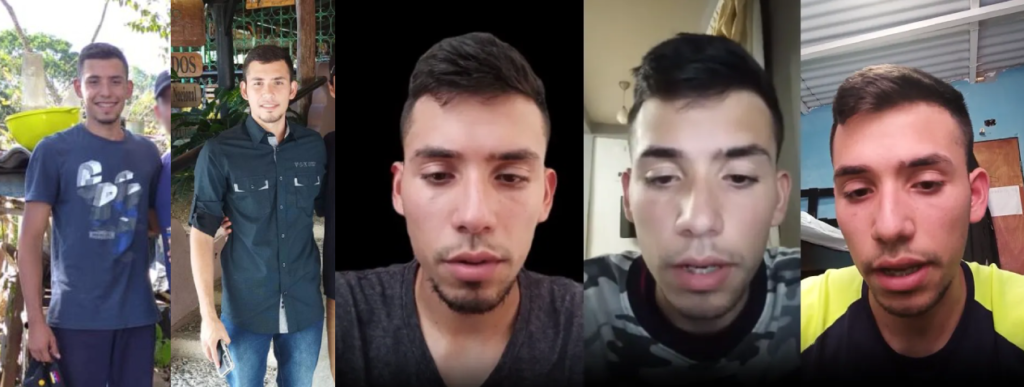
The criminal while he said on his Facebook that he made money from programming, he made money from child pornography and non-consensual pornography. the money came mostly from Exoclick ads
Not to mention the network of child pornography and non-consensual pornography Telegram groups that Johan Rodriguez owned and where he has also benefited from these groups flooded with illegal content.
Identity theft and fake LinkedIn accounts:
The pedophile is also engaged in the creation and purchase of LinkedIn accounts. As mentioned in the past, he asked on a hacker forum about hacked accounts of LinkedIn users. which is murky and suspicious.
The pedophile also creates Facebook pages and Twitter accounts, stealing the identities of mostly female celebrities to gain followers and sell their account on forums to users who want to buy old accounts.
CICPC and the Ministerio Público (Departament of Justice of Venezuela):
the CICPC (Cuerpo de Investigaciones Científicas, Penales y Criminalísticas) and the Ministerio Publico Office of Venezuela are organizations whose function is to catch and lock up criminals.
these organizations would be what the FBI and the Department of Justice are in the United States. In June, I sent the CICPC a confidential article showing all this research along with a lot of evidence of crimes related to child exploitation

When I sent the article with all the research to the email address provided by the cicpc.gob.ve some time later the email system sent me an email where it sent information that the system was down. so the email addresses didn’t work.
After this I went to the website of the governmental organization called CICPC, I realized that they did not have HTTPS in the SSL of the website. meaning that the site was not secure. And I couldn’t find an alternative to contact the police.
That’s when I realized that the CICPC’s servers and email systems weren’t working well. Repeatedly I went to the website and it was down and I had to wait a few minutes or a few hours. But searching I found a way to contact them
When I saw the contact form to make online complaints on the CICPC website, I wrote the same text that I had written in the email next to my name, surname and email address. and then submit the information written in the form
As I write this article on February 22, 2024 the CICPC website is down, the servers issue is still bad even 6 months later. Going back to the form, they didn’t answer me at all and didn’t send me any response emails.
This is the problem of bureaucracy. Pedophile rings profit from this kind of thing. When someone like me tries to fight pedophilia and wants to send an online submit , they can’t because of the bureaucracy and the downed servers.
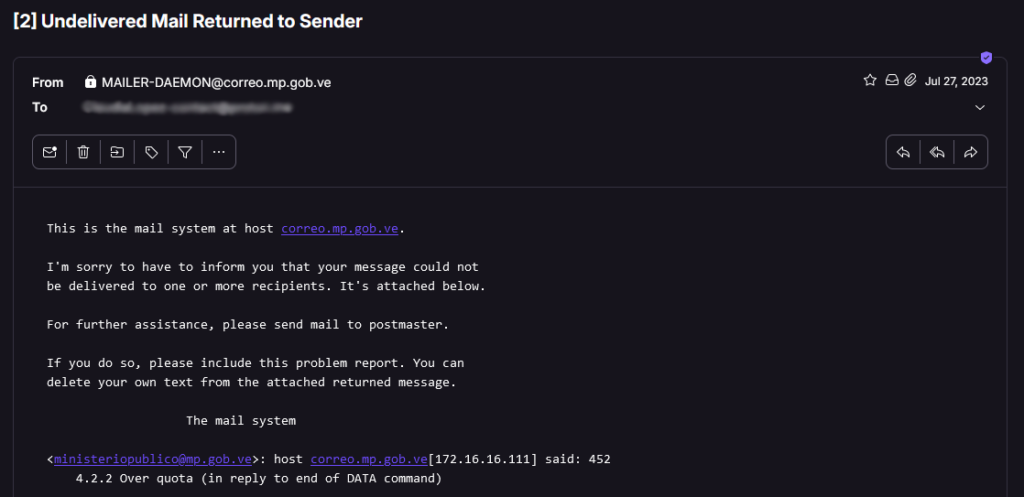
When looking for an alternative to contact the Venezuelan authorities, I contacted the Ministerio Publico of Venezuela by email address and when I sent emails on repeated occasions the Ministerio Publico server was down.
The people they affect are victims of child pornography and non-consensual pornography. A pedophile is free thanks to Venezuela’s bureaucracy.
OSINT tools used in the article:
All OSINT tools used to perform this operation written in this article. They are useful to carry out an entire research based on public fingerprints on the Internet
- Whois: ICANN Lookup , Whois Domain Lookup and History Whois
- obtain accounts linked to email address: SEON and OSINT INDUSTRIES
- Information of data breach linked to email: snusbase and have i been pwned
- domain analysis and backlinks: host.io – Domain Name Data
- The trusted source for IP address data: ipinfo.io
- OSINT in maps applications: OpenStreetMap and Google Maps
Internet services in response to this article:
Some internet services in response to this article suspended the accounts used by Johan Jose Rodriguez Moran. this is to remove any type of Child Sexual Abuse Material (CSAM) content or any reference to this child abuse content.

In case someone wants to report abuse to these same services, what they have to do is send an email to the abuse or support of these services. This is if you know of another case similar to this one in which these services are used.
- Wayback Machine: [email protected]
- Linkedin: [email protected]
- 4shared: Use this form to report inappropriate materials
- Medium: [email protected]
- WordPress: [email protected]
- Mega: [email protected]



Leave a Reply